A life of crime
Two years ago I read the book ‘American Kingpin: The Epic Hunt for the Criminal Mastermind Behind the Silk Road’. It is the story about the man who operated the Silk Road, a dark web marketplace where anyone could buy and sell anything. This rapidly became a drug haven of course, with people selling anything from weed to heroin.
This book spoke to me on a personal level, because I could imagine myself in a parallel reality taking a similar path, one where I would run a darkweb hacking empire. In fact, I’ve done some sketchy stuff as a teenager, so I thought it would be fun to portray some of them here. I don’t do these things any more, of course!
Scamming kids on Habbo Hotel
When I was 11, the hottest game that everyone was playing was Habbo Hotel. Habbo Hotel (it’s still around!) is a game where you socialize with your friends and random people. The most exciting part about it was that you could have your own hotel rooms, where you could customize the wallpaper, place furniture (known as ‘furni’) and keep pets. These customizations have to be bought of course, and all the cool kids in school would convince their parents to let them call the premium phone numbers, giving them virtual gold.
At the time I had already spend a bunch of time with Microsoft Frontpage, and learned a bit of HTML by looking at the HTML it would produce.
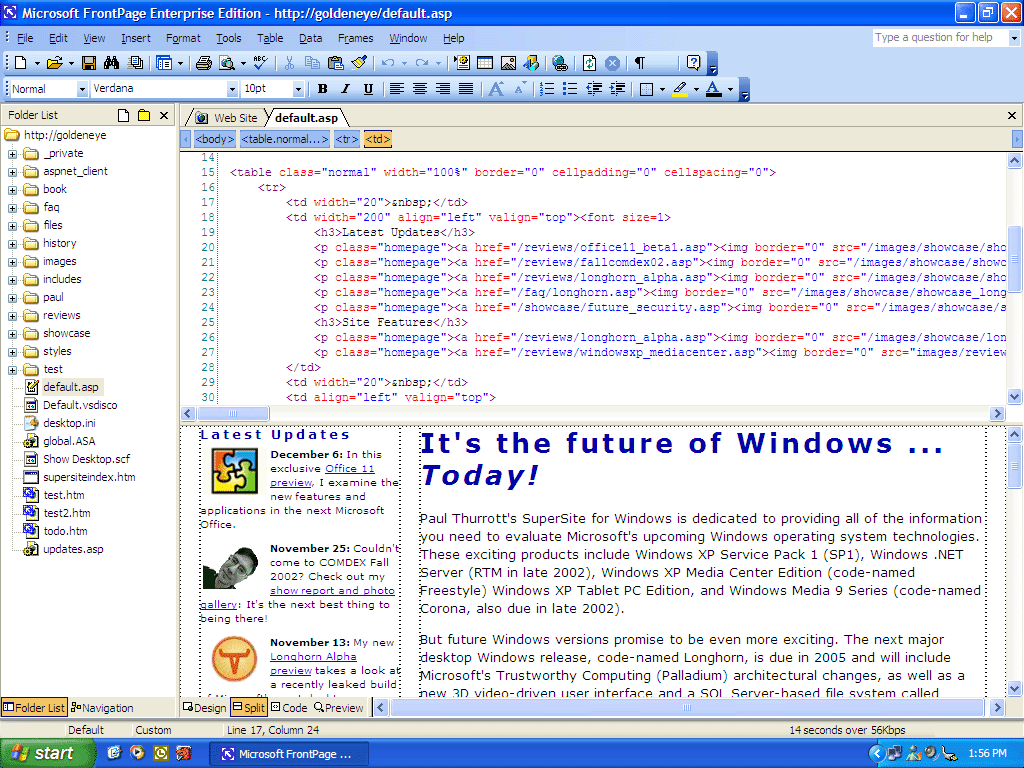
Armed with this rudimentary knowledge of HTML, I managed to copy the Habbo Hotel login page (by doing right click and save) and edit it to send the details people filled in to some free form service I found online. I then uploaded it to a free hosting service, which made it available online.
My friends and I would then log onto Habbo, create various characters with official-sounding names (think ‘KathyHelpHabbo’) and tell people to visit something like habbocredits.freewebhosting.com. And it worked! People would go there, fill in their log-in details, and we would receive the username and password by e-mail. We’d then log into their account, go to their rooms, take all the furniture and hand it over to our own accounts. In the end most of our accounts got banned, and in later years the creators put in various protections so you couldn’t just hand over all your furniture to other players, but we had a lot of fun while it lasted.
Reporting my teacher as sick with SQL injection
Around the age of 14 I started becoming more and more interested in hacking. Through online resources like HackThisSite.org I picked up some skills in breaking into websites.

With my primitive knowledge of web application hacking I started poking around on my school’s website. I came upon the login page for the rostering application they built, a typical in-house built script with all the warts you’d expect. Being the script kiddie I was at the time, I started copy and pasting from a list of SQL injections I found online. And to my delight, putting ' or '1'='1 into the password field worked! I was in.
With my newly gained access I could do two things: upload a new roster, or mark specific teachers as being sick. I opted for the most straightforward option, reporting my Dutch teacher as unavailable. This gave my class the first hour off! My whole class was hanging out in the lobby of the school, and we were having a good time as our Dutch teacher furiously passed us. In the end my access was short-lived, and the next day the vulnerability was fixed. Luckily I was never caught!
Hacking mobile games
At one point I became interested in reverse-engineering mobile apps, using tools like mitmproxy and apktool to figure out what was going on under the hood.
Draw Something
Draw Something is a game where two players take turns drawing a given word, which the other player then has to guess.

As you play the game you get a small number of coins every time you complete a game. These coins can be used to buy new colors to use during the game, and ‘bombs’ to make answering easier. Watching the traffic between the app and the server, I found out that it would simply access a /reward endpoint with your user ID! I wrote a script that would repeatedly give myself the maximum reward, giving me as many coins as I wanted without paying for the in-app purchase.
Songpop
Songpop is a 1-on-1 music quiz game, where you listen to music and answer questions about it.
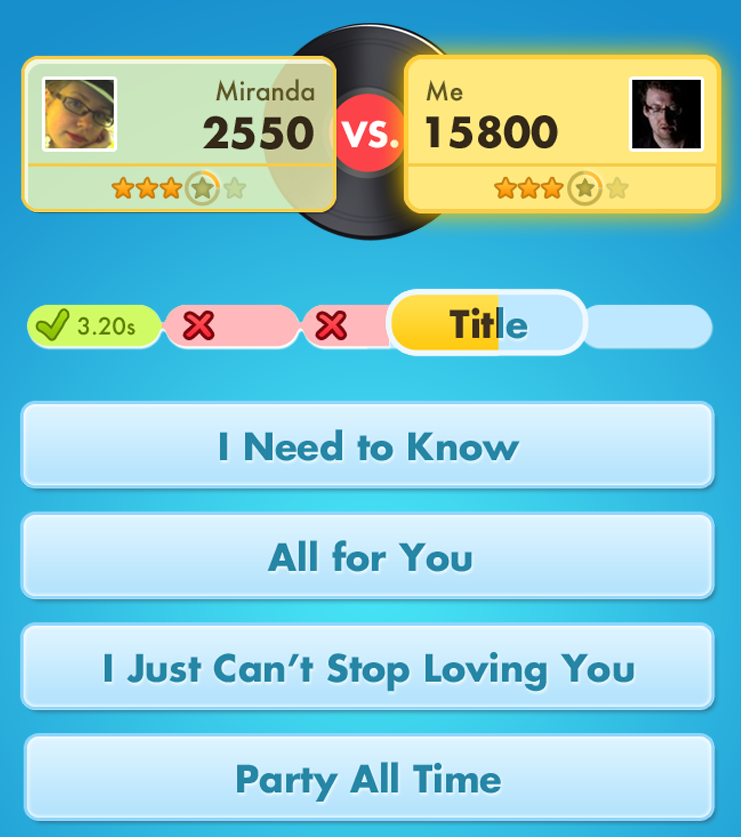
I was getting totally smoked by my classmates, so I pulled up mitmproxy and started inspecting the traffic that was being sent back and forth, and quickly realized that the answer was being sent with the question. Inspecting the traffic allowed me to view the answer beforehand, and I could even modify my reply to make the app think I took zero seconds, ensuring I would always get a maximum score.
Words With Friends
Words With Friends is a scrabble clone.
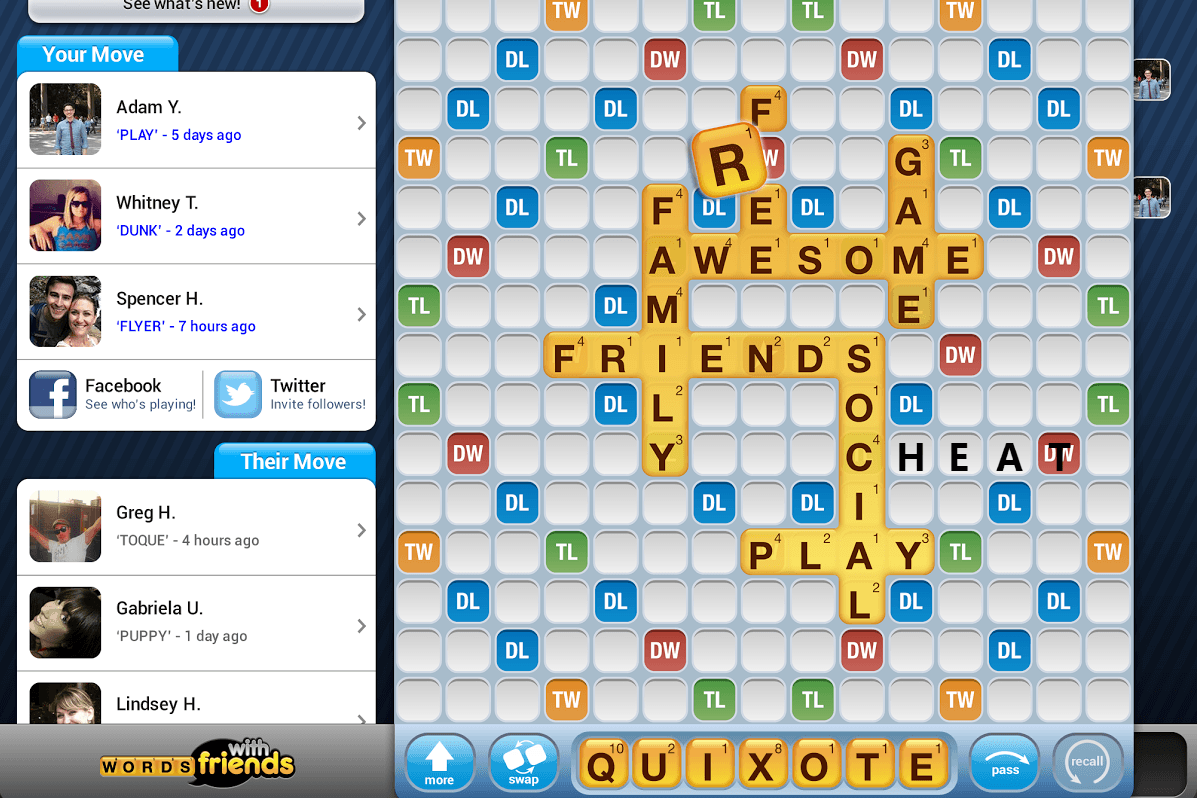
Using apktool I decompiled the application and started inspecting what was going on. Inside the application was a wordlist, which I edited to include a nonexistent word consisting of my whole rack of tiles, which to my great surprise worked! The words were only checked on the client-side, the server accepted any kind of submission. Nobody wanted to play with me after that.
Defacing my school
Two years after my first school hack, I hadn’t lost my appetite for breaking into things. I’d constantly try to figure out ways to break my school’s site, and then one day the school announced a contest to decide on a new slogan! All the students could submit suggestions for a slogan, and the school would pick out the one they liked best. If you’re creating PHP scripts from scratch then this is the perfect avenue for a very wide-spread category of bugs called Cross-Site Scripting (XSS). Instead of my submission just being
Fun and Educational!
I hid in some code, so I submitted
Fun and Educational!<script>evilCode()</script>
This extra bit of code would get executed when the administrator viewed the submissions, giving them no indication that anything malicious was going on. In my case I made the code take the cookies from the browser and send them to my email, so I could impersonate whoever viewed the submission. I diligently worked away on my exploit code, and submitted my ‘slogan’.
And then, I waited. I couldn’t know whether it worked, since there was no way to view your own submission after it was made. So I waited and waited. And then one afternoon: a hit! I received an email containing the cookies of the administrator. I put them into my browser and clicked refresh. It worked. I was now administrator of my school’s site.
What happened next is a bit of my blur in my mind. Since I only had the cookies, I needed a way to establish a permanent foothold into the site. I ran the risk of losing access once the session expired. I leafed through the various admin pages, until I found a seemingly neglected form that didn’t verify what type of file was being uploaded, and I used this to upload phpfm, the only PHP file access tool I could find that wouldn’t get blocked by the site’s virus scanners.
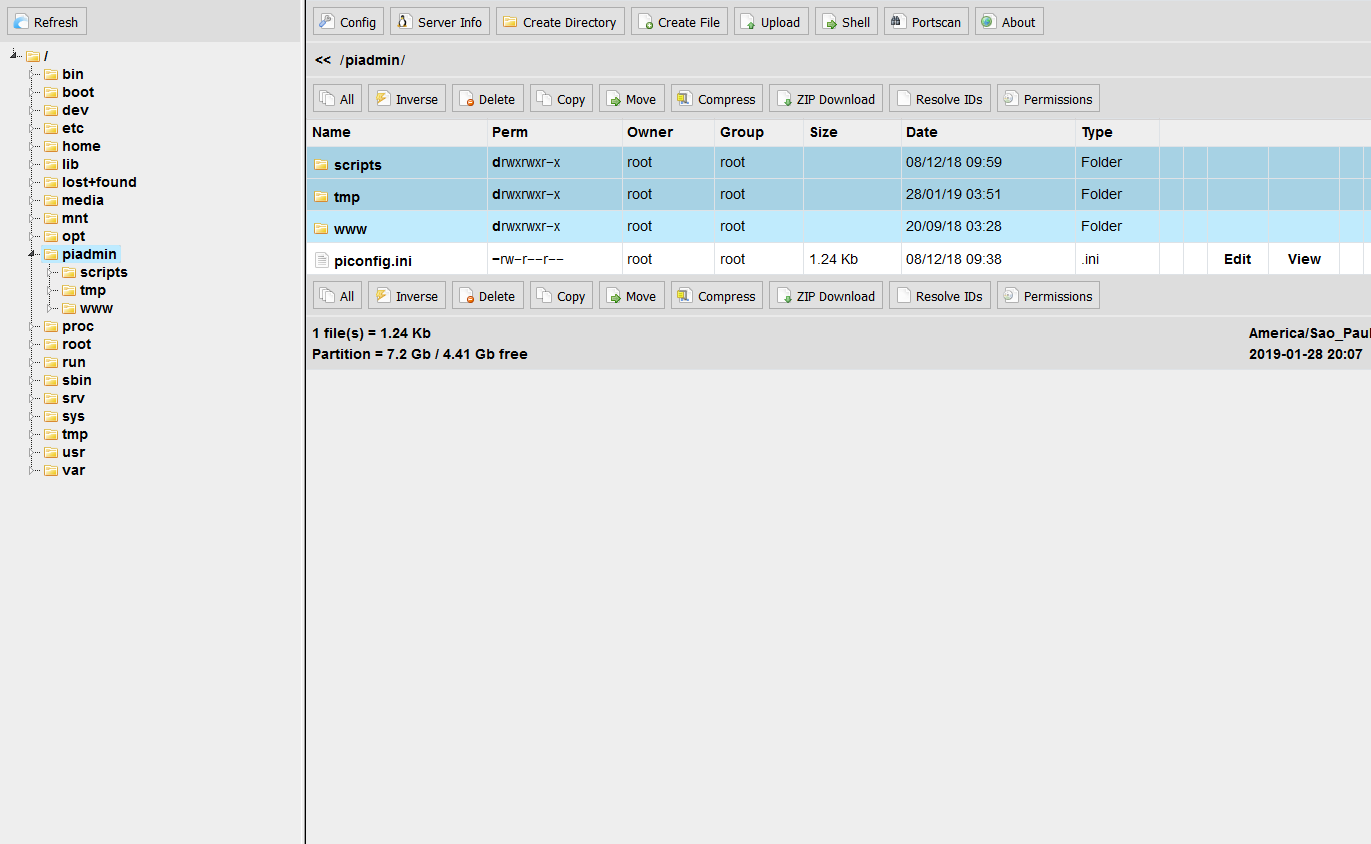
With this access in place, I was king. I could read every file, know every secret, break every code. I swiped the database credentials and downloaded the username and password of all the teacher and all the students. Of course, I didn’t tell anyone! But my vanity would become the end of me.
The fall
Maintaining my access to the site, I wasn’t really sure what to do next. Gaining access was the whole point, a temporary relieve from boredom without any malicious intent. During this time, I would organize LAN-parties with my friends. We would all get together at someone’s house, play some videogames and do a sleepover. During one of these parties, in an attempt to impress my friends, I perfomed the ultimate act in website hacking: I ‘defaced’ the site. ‘Defacing’ is an action where one clears out the whole website, replacing it with their own message. In my case it was something innocent, like ‘This site is not available, sorry :)’. Of course, for the people who needed the site for their job this was not so innocent, since it made it impossible for them to log-in.
I performed the defacing, my friends were mildly impressed, and we went on with playing videogames. The next day it was solved fairly quickly.
Monday rolls around and I’m back in class, pretending like nothing happened. During biology class the head of IT walks in, points to me and says ‘We need to talk!’, I knew exactly what was about to happen. Since I didn’t have any malicious intent, I spilled all the beans immediately, telling him exactly what I did, and showing where exactly I made my modifications. In the end I only got suspended for one day, which is about as well as it could’ve ended.
Aftermath
Thankfully I didn’t do anything too dangerous in the end, and didn’t get in too much trouble. These days I only hack by the book, having found other outlets to direct my energy towards. I do get a kick out of listening to Darknet Diaries though, which has many stories of kids pulling the same sort of stunts I did.
May 2019